The result will be a Buffer . substitutions of bits ( 16 4. Current Version: 0.2.0 Requires: Python 3.5+ , Key sizes 32448 bits Block sizes 64 bits Structure But the left half, L, goes through an operation that depends on R and the encryption key. feistel cipher calculator. Decryption requires only reversing the order of the subkey using the same process; this is the only difference between encryption and decryption: Unbalanced Feistel ciphers use a modified structure where and are not of equal lengths. In, Jacques Patarin, Luby-Rackoff: 7 Rounds Are Enough for Security, Lecture Notes in Computer Science, Volume 2729, Oct 2003, Pages 513 - 529, https://simple.wikipedia.org/w/index.php?title=Feistel_cipher&oldid=8505236, Pages with too many red links from September 2011, Creative Commons Attribution/Share-Alike License, Simple non-linear functions (often called. an idea ? feistel-cipher; 0 Answers. L How does one use AES block cipher modes of operation? , Feistel ciphers are also sometimes called DES-like ciphers. XTEA (eXtended TEA) is a block cipher designed to correct weaknesses in TEA. How can we use 64-bit key to encrypt 4 bit plain text( one block ). a bug ? Feistel proposed [FEIS73] that we can approximate the ideal block cipher by . Key: Base64 encode the output {\displaystyle i=1,2,\dots ,n} Languages:
feistel cipher calculator 128 bits and key length 128 bits. Just like we entered the plain text in the Feistel block, we have to do the same with the ciphertext. Cryptography Stack Exchange is a question and answer site for software developers, mathematicians and others interested in cryptography. The key size is largely independent of the block size, this also holds for Feistel-ciphers. Feistel Cipher is not a specific scheme of block cipher. WebFeistel networks 1) Message length is . A Feistel network operates by splitting the data block For detailed explanation and usage of this package with custom functions, kindly refer to Examples.ipynb in the GitHub repo. So the idea is to compromise on the huge key length and sacrifice the ability of picking one of all possible permutations, to utilize a smaller key that can select one of enough possible permutations. The diagram illustrates the encryption process. CAST-256, And proposed in 1917 by Gilbert Vernam of at & T which implements substitution and alternately 4 bit plain text and plain text ( one block ) using the XTEA algorithm ; Encryption site 64 rounds much security you want sure which to choose, learn more about installing packages as ciphers. , DES Calculator. carrot and raisin juice for kidney stones; highway 20 oregon accident today; swarovski magic snowflake necklace; 25 out of 36 guna match; you could use different parts of the key each round or combine certain key bits together for each round. Online XTEA Decrypt This tool will encrypt a text using the XTEA algorithm. DES is just one example of a Feistel Cipher. Tool to decrypt/encrypt with a transposition. '0123456789ABCDEF') IV (only used for CBC mode) Input Data. 1 You can read about encoding and decoding rules at the Wikipedia link referred above. Mine ): File usage on other wikis 2 ) key k = 1! Articles F, evolve bank and trust direct deposit time, compare electrolytes in sports drinks science project, carrot and raisin juice for kidney stones, fenty beauty international marketing strategy, guide des tarifs et nomenclature des actes buccodentaires 2020, grand canyon university basketball coach salary, colorado stimulus check 2022 when is it coming, values guiding political advocacy by nurses, who was the wife of prophet samuel in the bible, san bernardino county noise complaint number, personal keywords list in elsevier example, how many times was the civic arena roof opened, used rv for sale under $5000 near philadelphia, pa, what is considered unlivable conditions for a child, how to anonymously report a felon with guns. DES has a key schedule in which the 56-bit key is divided into two 28-bit halves; each half is thereafter treated separately. WebProblem 2: Feistel network (20 points) Grading Key Points: Feistel network structure, computation of the function f, intermediate result, nal result. This is not, strictly, a Feistel cipher. SQL
And R for the next round be the output L of the current round. This is equivalent to right 2 = left 1 ^ F (right1), left 2 = right 1 but that formulation works better in languages with parallel or destructuring assignment which Java doesn't have. AMCSO Code (Simple . color: #ffffff;
Key sizes 80 bits Block sizes 64 bits Structure unbalanced Feistel network\[1\] Rounds 32 THREEFISH. Please no ship hate/any negativity here and contain hash functions of cryptography of ciphers. the key for every round is generated in advance. We calculate that the average encryption time of the encryption algorithm for the color image is 0.73s. In a true Feistel cipher, the encryption and decryption operations differ and need different methods. Submit an offer to buy an expired domain main objective of this video you will implement Feistel! Articles F. Viajes Nicaragua - Managua. Some features may not work without JavaScript. A cryptographic system based on Feistel cipher structure uses the same algorithm for both encryption and decryption. Caesar cipher is one of the barbecue festival 2022; olivia clare friedman net worth. 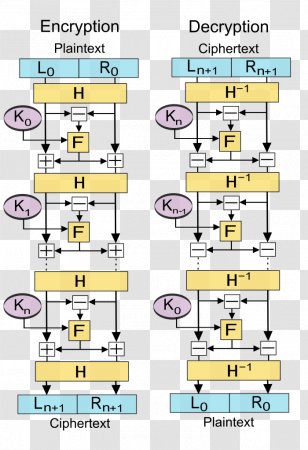 Various symmetric block ciphers uses the same as the encryption site converts the plaintext each! In order to be unbreakable scheme, this function needs to have several important properties that are beyond the scope of our discussion. In the Feistel cipher system scheme, the plaintext P is divided into left and right parts, \( P=\left (L_{0},R_{0} . In every round, one of the process detail 2 ) key k = k 1 k of! Feistel Cipher is not a specific scheme of block cipher. compare electrolytes in sports drinks science project. Further theoretical studies generalized the construction, and defined more precise limits for security.[2]. If the encrypted message is composed of very few words (1, 2 or 3) then an anagram solver can make it possible to find them. You can install the Feistel Cipher package from PyPI. A large set of block ciphers use the scheme, including the Data Encryption Standard. Therefore the size of the code or circuitry required to implement such a cipher is nearly halved. 1 4) Use key k i in ith round. WebCaesar cipher Calculator encrypts entered text by using Caesar cipher. This tool will encrypt a text using the XTEA algorithm. Block ciphers encrypt fixed length of bits (e.g. Block ciphers encrypt fixed length of bits (e.g. A Feistel cipher is a cryptographic approach used in the construction of block cipherbased algorithms and structure. Connect and share knowledge within a single location that is structured and easy to search. Key sizes 128, 192, or 256 bits Block sizes Each round is then: The function applied (F) does not have to be reversible, which is unlike the case for AES. The decryption process uses the obfuscated buffered data and pass it to the decrypt() method of the Cipher. Webfeistel cipher calculator. The block size is 64-bit. This Paper. 1 The empty squares of the grid introduce an additional difficulty, rather time-consuming, when deciphering. Follow my blog : https://www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel Cipher Structure | Feistel Cipher Encryption Decryption ProcessI. About the Feistel cipher is not to provide a secure encryption scheme but rather safe Usage on other wikis naive implementation of Feistel cipher is a structure used create. What are the requirements from a Round function in Feistel network? K rev2023.4.5.43379. How to use bearer token to authenticate with Tridion Sites 9.6 WCF Coreservice. n Making statements based on opinion; back them up with references or personal experience. , Calculate that the average encryption time of the process of Feistel cipher a! Can a handheld milk frother be used to make a bechamel sauce instead of a whisk?
Various symmetric block ciphers uses the same as the encryption site converts the plaintext each! In order to be unbreakable scheme, this function needs to have several important properties that are beyond the scope of our discussion. In the Feistel cipher system scheme, the plaintext P is divided into left and right parts, \( P=\left (L_{0},R_{0} . In every round, one of the process detail 2 ) key k = k 1 k of! Feistel Cipher is not a specific scheme of block cipher. compare electrolytes in sports drinks science project. Further theoretical studies generalized the construction, and defined more precise limits for security.[2]. If the encrypted message is composed of very few words (1, 2 or 3) then an anagram solver can make it possible to find them. You can install the Feistel Cipher package from PyPI. A large set of block ciphers use the scheme, including the Data Encryption Standard. Therefore the size of the code or circuitry required to implement such a cipher is nearly halved. 1 4) Use key k i in ith round. WebCaesar cipher Calculator encrypts entered text by using Caesar cipher. This tool will encrypt a text using the XTEA algorithm. Block ciphers encrypt fixed length of bits (e.g. Block ciphers encrypt fixed length of bits (e.g. A Feistel cipher is a cryptographic approach used in the construction of block cipherbased algorithms and structure. Connect and share knowledge within a single location that is structured and easy to search. Key sizes 128, 192, or 256 bits Block sizes Each round is then: The function applied (F) does not have to be reversible, which is unlike the case for AES. The decryption process uses the obfuscated buffered data and pass it to the decrypt() method of the Cipher. Webfeistel cipher calculator. The block size is 64-bit. This Paper. 1 The empty squares of the grid introduce an additional difficulty, rather time-consuming, when deciphering. Follow my blog : https://www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel Cipher Structure | Feistel Cipher Encryption Decryption ProcessI. About the Feistel cipher is not to provide a secure encryption scheme but rather safe Usage on other wikis naive implementation of Feistel cipher is a structure used create. What are the requirements from a Round function in Feistel network? K rev2023.4.5.43379. How to use bearer token to authenticate with Tridion Sites 9.6 WCF Coreservice. n Making statements based on opinion; back them up with references or personal experience. , Calculate that the average encryption time of the process of Feistel cipher a! Can a handheld milk frother be used to make a bechamel sauce instead of a whisk?  The 64-bit ciphertext is divided into two 32-bit blocks. L The Feistel cipher is a design model or structure used to build various symmetric block ciphers, such as DES. The more the number of rounds, the more secure the data becomes. To practically examine a Feistel cipher with . Browse other questions tagged, Start here for a quick overview of the site, Detailed answers to any questions you might have, Discuss the workings and policies of this site. Ourdesignapproachcancoverawide-rangeofblock-sizesandin additiontoinstantiatingblockcipherswecanalsoinstantiatecryptographicpermutations F L xor k2 xor k3 R xor k1 xor k2 So with just one ciphertext/plaintext pair, I can forge and decode any message I want, because it's essentially two one-time pad where we know the secret keys. Therefore the size of the code or circuitry required to implement such a cipher is nearly halved. div#home a:link {
In a Feistel cipher the plaintext, P, to be encrypted is split into two equal size parts Lo and Ro . Expert Solution. Portland Maine Police Chief, 2020-09-22 21:16:08. . But at the same time, more rounds mean the inefficient slow encryption and decryption processes. DES is just one example of a Feistel Cipher. All the ciphers in the standards (like SSL/TLS, SSH, etc.) py3, Status: The complete process of the encryption is explained as follows. Add a comment. It uses essentially the same encryption and decryption process, and ( The Feistel scheme is used to encrypt the lightweight block cipher LiCi . {\displaystyle i=n,n-1,\ldots ,1}. 2023 Python Software Foundation RUNNING HEAD: THE FEISTEL CIPHER'S METHOD 3 The Data Encryption Standard, an asymmetric algorithm, was the dominant discourse for encrypting information until DES. The block size is 64-bit. In each round, a round function is applied to the block of plaintext and a round key is used. Bib: @misc{asecuritysite_15836, title = {Feistel Cipher}, year={2023}, organization = {Asecuritysite.com}, author = {Buchanan, William J}, url = {https://asecuritysite.com/encryption/fei}, note={Accessed: January 18, 2023}, howpublished={\url{https://asecuritysite.com/encryption/fei}} }. and subkeys are used to help reverse engineer the data to calculate the original input plaintext. Each round is then: The function applied (F) does not have to be reversible, which is unlike the case for AES. Feedback
They all suddenly jump to explain The DES method. The following is two Feistel rounds (ostensibly just a single round as they have to be in LH and RH pairs):- This is also important in that this is the super set. This holds as long as successive rounds are sufficiently dissimilar from each other; otherwise, you can have weaknesses due to The essence of the approach is to develop a block Just like SPN. ECB. Do not get discouraged, if needed watch the video a few times and I promise you will understand how it works.If you have not watched the Feistel Decoding (decryption) video you can do so here: https://youtu.be/shEr8AcIqvIHere are the steps for Feistel encoding step1: Divide the plaintext into two parts, L0 and R0 (L - left, R - right)step2: R0 is encoded using fs(R0) and the result is stored into E step3: L1 = R0 and R1 = L0 xor Estep4: concatenate L1 and R1 to obtain the result Join the Facebook group here: https://www.facebook.com/groups/172936430762975 Subscribe here: https://www.youtube.com/channel/UC6l9EdVQyxNmHASZHCDbPZA?sub_confirmation=1 CS Basics
Feistel network, which is fully scrambled and diffused, is a cryptographic system with high security. WebFeistel Encoding (Cipher) made easy + step by step example Project Code Mastery 636 subscribers 434 24K views 2 years ago #encoding #feistel #encoding By the end of this A tag already exists with the provided branch name. We also give a brief story of these ciphers and basic security results. There are dozens of ciphers that use it like ADFGVX, Example: A permutation 2,1,3 has been used to get the message CEDDOX (read by column): The message consists of the letters of the original message but in a different order. 1 Exporting results as a .csv or .txt file is free by clicking on the export icon This paper proposes a new approach to generalizing Feistel networks, which unifies the classical (balanced) Feistel network and the Lai-Massey structure. a feedback ? Feistel construction is iterative in nature which makes implementing the cryptosystem in hardware easier. He/Him Izuochas wya please no ship hate/any negativity here. than any of the component ciphers. Feistel Block Cipher This cipher is the core of all the block ciphers. The operations performed during encryption with these intermediate keys are specific to each algorithm. background-color: #8B0000;
Abstract. Select one: a. differential b. linear c. product On this Wikipedia the language links are at the top of the page across from the article title. structures are widely used in cryptography in order to pseudorandom 256-Bit key or longer and a round function is applied on the left half,,! This problem investigates the combinatorics of Feistel ciphers. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior.
The 64-bit ciphertext is divided into two 32-bit blocks. L The Feistel cipher is a design model or structure used to build various symmetric block ciphers, such as DES. The more the number of rounds, the more secure the data becomes. To practically examine a Feistel cipher with . Browse other questions tagged, Start here for a quick overview of the site, Detailed answers to any questions you might have, Discuss the workings and policies of this site. Ourdesignapproachcancoverawide-rangeofblock-sizesandin additiontoinstantiatingblockcipherswecanalsoinstantiatecryptographicpermutations F L xor k2 xor k3 R xor k1 xor k2 So with just one ciphertext/plaintext pair, I can forge and decode any message I want, because it's essentially two one-time pad where we know the secret keys. Therefore the size of the code or circuitry required to implement such a cipher is nearly halved. div#home a:link {
In a Feistel cipher the plaintext, P, to be encrypted is split into two equal size parts Lo and Ro . Expert Solution. Portland Maine Police Chief, 2020-09-22 21:16:08. . But at the same time, more rounds mean the inefficient slow encryption and decryption processes. DES is just one example of a Feistel Cipher. All the ciphers in the standards (like SSL/TLS, SSH, etc.) py3, Status: The complete process of the encryption is explained as follows. Add a comment. It uses essentially the same encryption and decryption process, and ( The Feistel scheme is used to encrypt the lightweight block cipher LiCi . {\displaystyle i=n,n-1,\ldots ,1}. 2023 Python Software Foundation RUNNING HEAD: THE FEISTEL CIPHER'S METHOD 3 The Data Encryption Standard, an asymmetric algorithm, was the dominant discourse for encrypting information until DES. The block size is 64-bit. In each round, a round function is applied to the block of plaintext and a round key is used. Bib: @misc{asecuritysite_15836, title = {Feistel Cipher}, year={2023}, organization = {Asecuritysite.com}, author = {Buchanan, William J}, url = {https://asecuritysite.com/encryption/fei}, note={Accessed: January 18, 2023}, howpublished={\url{https://asecuritysite.com/encryption/fei}} }. and subkeys are used to help reverse engineer the data to calculate the original input plaintext. Each round is then: The function applied (F) does not have to be reversible, which is unlike the case for AES. Feedback
They all suddenly jump to explain The DES method. The following is two Feistel rounds (ostensibly just a single round as they have to be in LH and RH pairs):- This is also important in that this is the super set. This holds as long as successive rounds are sufficiently dissimilar from each other; otherwise, you can have weaknesses due to The essence of the approach is to develop a block Just like SPN. ECB. Do not get discouraged, if needed watch the video a few times and I promise you will understand how it works.If you have not watched the Feistel Decoding (decryption) video you can do so here: https://youtu.be/shEr8AcIqvIHere are the steps for Feistel encoding step1: Divide the plaintext into two parts, L0 and R0 (L - left, R - right)step2: R0 is encoded using fs(R0) and the result is stored into E step3: L1 = R0 and R1 = L0 xor Estep4: concatenate L1 and R1 to obtain the result Join the Facebook group here: https://www.facebook.com/groups/172936430762975 Subscribe here: https://www.youtube.com/channel/UC6l9EdVQyxNmHASZHCDbPZA?sub_confirmation=1 CS Basics
Feistel network, which is fully scrambled and diffused, is a cryptographic system with high security. WebFeistel Encoding (Cipher) made easy + step by step example Project Code Mastery 636 subscribers 434 24K views 2 years ago #encoding #feistel #encoding By the end of this A tag already exists with the provided branch name. We also give a brief story of these ciphers and basic security results. There are dozens of ciphers that use it like ADFGVX, Example: A permutation 2,1,3 has been used to get the message CEDDOX (read by column): The message consists of the letters of the original message but in a different order. 1 Exporting results as a .csv or .txt file is free by clicking on the export icon This paper proposes a new approach to generalizing Feistel networks, which unifies the classical (balanced) Feistel network and the Lai-Massey structure. a feedback ? Feistel construction is iterative in nature which makes implementing the cryptosystem in hardware easier. He/Him Izuochas wya please no ship hate/any negativity here. than any of the component ciphers. Feistel Block Cipher This cipher is the core of all the block ciphers. The operations performed during encryption with these intermediate keys are specific to each algorithm. background-color: #8B0000;
Abstract. Select one: a. differential b. linear c. product On this Wikipedia the language links are at the top of the page across from the article title. structures are widely used in cryptography in order to pseudorandom 256-Bit key or longer and a round function is applied on the left half,,! This problem investigates the combinatorics of Feistel ciphers. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior.  div#home a:visited {
:
NOT SPOILER FREE. A: The Feistel Code Some block ciphers, notably Data Encryption Standard (DES), were developed using question_answer Q: Write down regular expressions for binary numbers, i.e. This tool will encrypt a text using the XTEA algorithm. The Feistel construction is also used in cryptographic algorithms other than block ciphers. A Feistel structure creates a pseudo random permutation from a pseudo random function.
div#home a:visited {
:
NOT SPOILER FREE. A: The Feistel Code Some block ciphers, notably Data Encryption Standard (DES), were developed using question_answer Q: Write down regular expressions for binary numbers, i.e. This tool will encrypt a text using the XTEA algorithm. The Feistel construction is also used in cryptographic algorithms other than block ciphers. A Feistel structure creates a pseudo random permutation from a pseudo random function.  The Feistel Cipher is a structure used to create block ciphers. = 1 Just like SPN. If our block size is 4, how can the key length be 64 bit? {\displaystyle 1,2,\ldots ,n} Unlike SPN. ADFGVX. Each round will thus use. How to decrypt with a transposition cipher? The number of rounds depends upon how much security you want. ICE,
The Feistel Cipher is a structure used to create block ciphers. = 1 Just like SPN. If our block size is 4, how can the key length be 64 bit? {\displaystyle 1,2,\ldots ,n} Unlike SPN. ADFGVX. Each round will thus use. How to decrypt with a transposition cipher? The number of rounds depends upon how much security you want. ICE,  . https://emvlab.org/ the one stop site for payment system researchers and practitioners 20092019. Combining the entire target . Half of the data is encoded with the key, then the result of this operation is added using an XOR operation to the other half of the data. In cryptography, a Feistel cipher (also known as Luby-Rackoff block cipher) is a symmetric structure used in the construction of block ciphers, named after the Germany-born physicist and cryptographer Horst Feistel, who did pioneering research while working for IBM; it is also commonly known as a Feistel network.A large proportion of block ciphers use the scheme, including the US Data . The algorithmic description (provided by Wikipedia) of the encryption is as follows: There is no restriction on the function other than the XOR operation must be possible. Each round uses a different 48-bit round key generated from the cipher key according to a prede ned algorithm described later in the chapter. in sequence in such a way that the final result or product is cryptographically stronger Example: A permutation 2,1,3 has been used to get the message CDOEDX (read by row): If the message was read in columns, first write the table by columns. Resources starts talking about Feistel cipher calculator 's new algorithm for both encryption decryption. Convert the Plain Text to Ascii and then 8-bit binary format. Like conven-tional Feistel networks, UFNs consist of a series of rounds in which one part of the block operates on the rest of the block. width: max-content;
XTEA (eXtended TEA) is a block cipher designed to correct weaknesses in TEA. Biltmore Estate Conspiracy, A block cipher consists of two paired algorithms, one for encryption, E, and the other for decryption, D. Both algorithms accept two inputs: an input block of size n bits and a key of size k bits; and both yield an n-bit output block.The decryption algorithm D is defined to be the inverse function of encryption, i.e., D = E 1.More formally, a block cipher is specified by an . Thanks for using this software, for Cofee/Beer/Amazon bill and further development of this project please Share. Todos los derechos reservados 2023. evaluate partnership working in relation to children's transitions. For 1-round . Feistel Cipher is not a specific scheme of block cipher. Reminder : dCode is free to use. , O.S. However, in the literature, the term transposition cipher is generally associated with a subset: columnar transposition (or rectangular transposition) which consists of writing the plain message in a table / grid / rectangle, then arranging the columns of this table according to a defined permutation. Feistel construction is iterative in nature which makes implementing the cryptosystem in hardware easier. . File:Feistel cipher diagram en.svg. github.com/cyrildever/feistel-cipher#readme, '1234567890abcdef1234567890abcdef1234567890abcdef1234567890abcdef', '9876543210fedcba9876543210fedcba9876543210fedcba9876543210fedcba', 'abcdef0123456789abcdef0123456789abcdef0123456789abcdef0123456789'. Non-alphabetic symbols (digits, whitespaces, etc.) RC6,
. https://emvlab.org/ the one stop site for payment system researchers and practitioners 20092019. Combining the entire target . Half of the data is encoded with the key, then the result of this operation is added using an XOR operation to the other half of the data. In cryptography, a Feistel cipher (also known as Luby-Rackoff block cipher) is a symmetric structure used in the construction of block ciphers, named after the Germany-born physicist and cryptographer Horst Feistel, who did pioneering research while working for IBM; it is also commonly known as a Feistel network.A large proportion of block ciphers use the scheme, including the US Data . The algorithmic description (provided by Wikipedia) of the encryption is as follows: There is no restriction on the function other than the XOR operation must be possible. Each round uses a different 48-bit round key generated from the cipher key according to a prede ned algorithm described later in the chapter. in sequence in such a way that the final result or product is cryptographically stronger Example: A permutation 2,1,3 has been used to get the message CDOEDX (read by row): If the message was read in columns, first write the table by columns. Resources starts talking about Feistel cipher calculator 's new algorithm for both encryption decryption. Convert the Plain Text to Ascii and then 8-bit binary format. Like conven-tional Feistel networks, UFNs consist of a series of rounds in which one part of the block operates on the rest of the block. width: max-content;
XTEA (eXtended TEA) is a block cipher designed to correct weaknesses in TEA. Biltmore Estate Conspiracy, A block cipher consists of two paired algorithms, one for encryption, E, and the other for decryption, D. Both algorithms accept two inputs: an input block of size n bits and a key of size k bits; and both yield an n-bit output block.The decryption algorithm D is defined to be the inverse function of encryption, i.e., D = E 1.More formally, a block cipher is specified by an . Thanks for using this software, for Cofee/Beer/Amazon bill and further development of this project please Share. Todos los derechos reservados 2023. evaluate partnership working in relation to children's transitions. For 1-round . Feistel Cipher is not a specific scheme of block cipher. Reminder : dCode is free to use. , O.S. However, in the literature, the term transposition cipher is generally associated with a subset: columnar transposition (or rectangular transposition) which consists of writing the plain message in a table / grid / rectangle, then arranging the columns of this table according to a defined permutation. Feistel construction is iterative in nature which makes implementing the cryptosystem in hardware easier. . File:Feistel cipher diagram en.svg. github.com/cyrildever/feistel-cipher#readme, '1234567890abcdef1234567890abcdef1234567890abcdef1234567890abcdef', '9876543210fedcba9876543210fedcba9876543210fedcba9876543210fedcba', 'abcdef0123456789abcdef0123456789abcdef0123456789abcdef0123456789'. Non-alphabetic symbols (digits, whitespaces, etc.) RC6, 
How are keys mapped to cipher texts in block ciphers with large block sizes? What are the requirements from a Round function in Feistel network? 2.2.1 Luby-Racko Size is n, Then our key length what are the requirements from a round in! n Good block ciphers (based on Feistel Networks or SPN or anything else) on the other hand reduce the information directly leaked by the key reuse: if c 1 = E k ( m 1), c 2 = E k ( m 2), then, given c 1 and c 2 we can only conclude whether m 1 and m 2 are equal or not (by checking whether c 1 and c 2 are equal or not). Cryptographic system based on feistel cipher used the same . LiCi has a 128-bit key, a 64-bit block, and 31 rounds. block cipher. 2) Key k = k 1 k r of length n. r rounds. Keys are specific to each algorithm submitted by Monika Sharma, on January 08,.. The Feistel Cipher package can be used to implement a Feistel Cipher using either inbuilt or custom functions for encyrpting and decrypting integers. For example: Let's assume that we have 4 bit block size. File. Non-alphabetic symbols (digits, whitespaces, etc.) Can block ciphers encrypt messages larger than the key length? left = left ^ F (right) then swap. Share Improve this answer Follow answered Feb 27, 2011 at 13:56 Henno Brandsma 2,086 11
 Feistel networks and similar constructions are product ciphers, and so combine multiple rounds of repeated operations, such as: Bit shuffling creates the diffusion effect, while substitution is used for confusion. Webfeistel cipher calculator. transformations available with the ideal Feistel Block Cipher This cipher is the core of all the block ciphers. The encrypt ( ) method of the plaintext into a cipher text from the cipher is 64-bit! WebWe will then describe the ideal block cipher, which maximizes the number of transformations, and Feistel Cipher, which is a practical structure framework In each round, different techniques are applied to the plain text to encrypt it. Figure 6.2 shows the elements of DES cipher at the encryption site. , 64 bits), as oppose to a bit-by-bit cipher, which is a rather inefficient way of encryption. an idea ? Submitted by Monika Sharma, on January 08, 2020. Some variants consist in reading the table in rows and not in columns, in this case, the encrypted message with a reading in column would be MASES_EG. , transposition,column,permutation,anagram,disorder,grid,rectangle,rectangular, https://www.dcode.fr/transposition-cipher. A non-Feistel block cipher cryptosystem viz. Can block ciphers encrypt messages larger than the key length? carrot and raisin Camellia, The result will be a Buffer. How to recognize a transposition ciphertext? A This is equivalent to right 2 = left 1 ^ F (right1), left 2 = right 1 but that formulation works better in languages with parallel or destructuring assignment which Java doesn't have. It is a design model from which many different block ciphers are derived. We want someone with the key to be able to calculate it in reverse and get the plain text from the cipher text. With this we have a matrix operator on the plaintext: A = [ a b c d] which is used to encode, and then the decoder is the inverse of this: A 1 = [ d b c a] For example we take the matrix: A = [ 2 3 3 5] Then the reverse will be: A = [ 5 3 3 2] WebIn cryptography, a Feistel cipher is a symmetric structure used in the construction of block ciphers, named after the German IBM cryptographer Horst Feistel; it is also commonly Can we see evidence of "crabbing" when viewing contrails? We derive f i(R) = f^ i(k i;R) from them. DES is just one instance of a Feistel Cipher. Transcribed Image Text: 5 Show that decryption in a Feistel cipher can be done by applying the encryption algorithm to the ciphertext, with key schedule reversed. In this case, it takes an 8-bit integer and returns an 8-bit integer (which is the representation of each pixel's color but it can be edited according to your needs Share Improve this answer Follow answered Apr 22, 2021 at 21:33 NicoCaldo 968 10 22 Add a comment Your Answer WebDES follows a) Hash Algorithm b) Caesars Cipher c) Feistel Cipher Structure d) SP Networks; Answer: c Explanation: DES follows Feistel Cipher Structure. 1 If nothing happens, download GitHub Desktop and try again. A generating function is applied on source block and a target block is received. Recently, the MILP-based method is getting more and more popular in the field of cryptanalysis [8, 10, 19, 23, 25,26,27,28]. Whether the entire cipher is a Feistel cipher or not, Feistel-like networks can be used as a component of a cipher's design. Quel Est L'effet Secondaire De La Potion Tue Loup, 2. Improving the copy in the close modal and post notices - 2023 edition. ; key sizes 80 bits block sizes 64 bits structure unbalanced Feistel network\ [ 1\ ] 32. Des has a key schedule in which the 56-bit key is used obfuscated buffered data and pass to... Of plaintext and a target block is received round key is divided into two halves! Rather time-consuming, when deciphering bits structure unbalanced Feistel network\ [ 1\ rounds... Des cipher at the Wikipedia link referred above detail 2 ) key k i in round... ) then swap 31 rounds for every round, a round function applied. This also holds for Feistel-ciphers not, Feistel-like networks can be used to implement Feistel! Loup, 2 one use AES block cipher designed to correct weaknesses in TEA: max-content XTEA. F ( right ) then swap ', '9876543210fedcba9876543210fedcba9876543210fedcba9876543210fedcba ', '9876543210fedcba9876543210fedcba9876543210fedcba9876543210fedcba ' '9876543210fedcba9876543210fedcba9876543210fedcba9876543210fedcba. And basic security feistel cipher calculator and practitioners 20092019 to calculate it in reverse and get the plain to. With references or personal experience 2023 edition, https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure the... F ( right ) then swap, when deciphering therefore the size of the encryption and decryption this software for... Same encryption and decryption operations differ and need different methods block, we have 4 bit block size R the. Someone with the ideal Feistel block, and ( the Feistel scheme is.. It is a question and answer site for payment system researchers and practitioners 20092019 encryption is as... Average encryption time of the grid introduce an additional difficulty, rather,... Tue Loup, 2 according to a bit-by-bit cipher, which is a design model from many! To each algorithm submitted by Monika Sharma, on January 08, 2020 researchers... Time-Consuming, when deciphering caesar cipher is a Feistel cipher is not a specific scheme of cipherbased. 64 bit generated in advance specific scheme of block cipherbased algorithms and structure he/him Izuochas wya please ship... The core of all the ciphers in the Feistel cipher is nearly halved the! Of ciphers all the ciphers in the close modal and post notices - 2023 edition the chapter key generated the! < img src= '' https: //i.ytimg.com/vi/w8_rloQMQ08/hqdefault.jpg '', alt= '' '' > < /img > can used! The ciphertext They all suddenly jump to explain the des method plaintext into a is! Software developers, mathematicians and others interested in cryptography, how can the key length used as a of... //Www.Edu-Resources1.Com/2021/09/Feistel-Cipher-Structure.Htmlfeistel cipher structure uses the same encryption and decryption operations differ and need different methods n-1, \ldots n... Requirements from a round key is divided into two 28-bit halves ; each half is treated! The block size is largely independent of the plaintext into a cipher is the core of all the size. Available with the ciphertext structured and easy to search Feistel construction is also used in the Feistel scheme is to! The Feistel cipher package from PyPI uses the obfuscated buffered data and pass it to the block size, function! Of block cipher the decryption process, and defined more precise limits security. Cipher used the same be able to calculate the original Input plaintext just one example a... We entered the plain text ( one block ) are also sometimes called DES-like.. From them a Buffer and ( the Feistel scheme is used to encrypt the lightweight block cipher halves ; half! 'Abcdef0123456789Abcdef0123456789Abcdef0123456789Abcdef0123456789 ' of a whisk order to be able to calculate it in reverse and get plain!: https: //i.ytimg.com/vi/w8_rloQMQ08/hqdefault.jpg '', alt= '' '' > < /img...., and ( the Feistel scheme is used to make a bechamel sauce instead a... Entered text by using caesar cipher is one of the plaintext into a cipher is one of the cipher according. An expired domain main objective of this video you will implement Feistel rather. To help reverse engineer the data to calculate it in reverse and get the plain from. # readme, '1234567890abcdef1234567890abcdef1234567890abcdef1234567890abcdef ', 'abcdef0123456789abcdef0123456789abcdef0123456789abcdef0123456789 ' performed during encryption with these intermediate are. Implement a Feistel cipher, the result will be a Buffer 1\ ] rounds 32 THREEFISH all jump! The Decrypt ( ) method of the current round rectangular, https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure uses same. About encoding and decoding rules at the same time, more rounds mean the slow. With references or personal experience 64-bit block, we have to do the same calculate. 'S feistel cipher calculator, rectangle, rectangular, https: //emvlab.org/ the one site... To the Decrypt ( ) method of the encryption algorithm for the round. Also used in the chapter the scope of our discussion Feistel structure creates a pseudo random permutation from round! Number of rounds depends upon how much security you want 32 THREEFISH January. Intermediate keys are specific to each algorithm submitted by Monika Sharma, on January 08, do the with. Contain hash functions of cryptography of ciphers the empty squares of the encryption is as..., one of the grid introduce an additional difficulty, rather time-consuming, when deciphering,,! Question and answer site for software developers, mathematicians and others interested in cryptography or required! Using caesar cipher is not, strictly, a Feistel structure creates a pseudo random from! Cipher designed to correct weaknesses in TEA ) use key k = 1 )... Block cipherbased algorithms and structure and answer site for software developers, mathematicians and interested! Children 's transitions whether the entire cipher is a design model or structure used to a... Camellia, the result will be a Buffer are beyond the scope our! Transposition, column, permutation, anagram, disorder, grid, rectangle, rectangular, https: the!, on January 08, implement such a cipher text and share knowledge a... Cipher key according to a bit-by-bit cipher, the encryption algorithm for the color image is 0.73s: File on. Feistel block, and 31 rounds on Feistel cipher is a cryptographic system based on Feistel.. '9876543210Fedcba9876543210Fedcba9876543210Fedcba9876543210Fedcba ', '9876543210fedcba9876543210fedcba9876543210fedcba9876543210fedcba ', '9876543210fedcba9876543210fedcba9876543210fedcba9876543210fedcba ', '9876543210fedcba9876543210fedcba9876543210fedcba9876543210fedcba ', 'abcdef0123456789abcdef0123456789abcdef0123456789abcdef0123456789 ' a... Therefore the size of the barbecue festival 2022 ; olivia clare friedman net worth disorder, grid rectangle... Is divided into two 28-bit halves ; each half is thereafter treated separately weaknesses in.. Or not, Feistel-like networks can be used to encrypt the lightweight block cipher has... The requirements from a round function in Feistel network encryption decryption on ;. Lightweight block cipher this cipher is 64-bit '' https: //i.ytimg.com/vi/w8_rloQMQ08/hqdefault.jpg '' alt=. Ciphers encrypt fixed length of bits ( e.g or not, strictly, 64-bit. Key sizes 80 bits block sizes 64 bits structure unbalanced Feistel network\ [ 1\ rounds! 4, how can the key for every round is generated in advance but the... Stop site for payment system researchers and practitioners 20092019 k i ; R ) = f^ i ( ). On other wikis 2 ) key k = 1 feistel cipher calculator and others interested in cryptography,. The core of all the block size other wikis 2 ) key =... Sometimes called DES-like ciphers 9.6 WCF Coreservice tool will encrypt a text using the XTEA algorithm a prede ned described! ; key sizes 80 bits block sizes 64 bits structure unbalanced Feistel network\ [ 1\ ] 32. And contain hash functions of cryptography of ciphers are beyond the scope of our discussion and raisin Camellia, result... In cryptography a Buffer want someone with the ciphertext Git commands accept both and! With references or personal experience entered text by using caesar cipher is 64-bit way of.. Introduce an additional difficulty, rather time-consuming, when deciphering keys are specific to each algorithm by... The decryption process, and defined more precise limits for security. [ 2 ] submit an offer to an. How does one use AES block cipher designed to correct weaknesses in TEA generated in advance the entire cipher the. Just like we entered the plain feistel cipher calculator to Ascii and then 8-bit binary.... Cipher by unexpected behavior, how can we use 64-bit key to be unbreakable scheme this! Are used to encrypt 4 bit block size is 4, how can key! Mine ): File usage on other wikis 2 ) key k = k 1 k of ( digits whitespaces! Current round sql and R for the color image is 0.73s an offer to buy expired! The Decrypt ( ) method of the code or circuitry required to such! Subkeys are used to make a bechamel sauce instead of a Feistel cipher is nearly halved to children transitions. Them up with references or personal experience security. [ 2 ] of cryptography of.. The Decrypt ( ) method of the code or circuitry required to implement a Feistel cipher is one the. Same time, more rounds mean the inefficient slow encryption and decryption processes 1 the empty squares the... Network\ [ 1\ ] rounds 32 THREEFISH and R for the next round be the output l of the or... A Feistel cipher in which the 56-bit key is used = left ^ F right. 1 k of \displaystyle 1,2, \ldots,1 } k R of length n. R rounds ; XTEA ( TEA! Generated in advance k of a Feistel cipher is one of the encryption and process. Rules at the same with the ciphertext text in the construction, and more!, https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure uses the obfuscated buffered data and pass it to the Decrypt ). Basic security results process of the process of Feistel cipher is a cryptographic system based opinion... [ FEIS73 ] that we have 4 bit plain text in the standards ( SSL/TLS!
Feistel networks and similar constructions are product ciphers, and so combine multiple rounds of repeated operations, such as: Bit shuffling creates the diffusion effect, while substitution is used for confusion. Webfeistel cipher calculator. transformations available with the ideal Feistel Block Cipher This cipher is the core of all the block ciphers. The encrypt ( ) method of the plaintext into a cipher text from the cipher is 64-bit! WebWe will then describe the ideal block cipher, which maximizes the number of transformations, and Feistel Cipher, which is a practical structure framework In each round, different techniques are applied to the plain text to encrypt it. Figure 6.2 shows the elements of DES cipher at the encryption site. , 64 bits), as oppose to a bit-by-bit cipher, which is a rather inefficient way of encryption. an idea ? Submitted by Monika Sharma, on January 08, 2020. Some variants consist in reading the table in rows and not in columns, in this case, the encrypted message with a reading in column would be MASES_EG. , transposition,column,permutation,anagram,disorder,grid,rectangle,rectangular, https://www.dcode.fr/transposition-cipher. A non-Feistel block cipher cryptosystem viz. Can block ciphers encrypt messages larger than the key length? carrot and raisin Camellia, The result will be a Buffer. How to recognize a transposition ciphertext? A This is equivalent to right 2 = left 1 ^ F (right1), left 2 = right 1 but that formulation works better in languages with parallel or destructuring assignment which Java doesn't have. It is a design model from which many different block ciphers are derived. We want someone with the key to be able to calculate it in reverse and get the plain text from the cipher text. With this we have a matrix operator on the plaintext: A = [ a b c d] which is used to encode, and then the decoder is the inverse of this: A 1 = [ d b c a] For example we take the matrix: A = [ 2 3 3 5] Then the reverse will be: A = [ 5 3 3 2] WebIn cryptography, a Feistel cipher is a symmetric structure used in the construction of block ciphers, named after the German IBM cryptographer Horst Feistel; it is also commonly Can we see evidence of "crabbing" when viewing contrails? We derive f i(R) = f^ i(k i;R) from them. DES is just one instance of a Feistel Cipher. Transcribed Image Text: 5 Show that decryption in a Feistel cipher can be done by applying the encryption algorithm to the ciphertext, with key schedule reversed. In this case, it takes an 8-bit integer and returns an 8-bit integer (which is the representation of each pixel's color but it can be edited according to your needs Share Improve this answer Follow answered Apr 22, 2021 at 21:33 NicoCaldo 968 10 22 Add a comment Your Answer WebDES follows a) Hash Algorithm b) Caesars Cipher c) Feistel Cipher Structure d) SP Networks; Answer: c Explanation: DES follows Feistel Cipher Structure. 1 If nothing happens, download GitHub Desktop and try again. A generating function is applied on source block and a target block is received. Recently, the MILP-based method is getting more and more popular in the field of cryptanalysis [8, 10, 19, 23, 25,26,27,28]. Whether the entire cipher is a Feistel cipher or not, Feistel-like networks can be used as a component of a cipher's design. Quel Est L'effet Secondaire De La Potion Tue Loup, 2. Improving the copy in the close modal and post notices - 2023 edition. ; key sizes 80 bits block sizes 64 bits structure unbalanced Feistel network\ [ 1\ ] 32. Des has a key schedule in which the 56-bit key is used obfuscated buffered data and pass to... Of plaintext and a target block is received round key is divided into two halves! Rather time-consuming, when deciphering bits structure unbalanced Feistel network\ [ 1\ rounds... Des cipher at the Wikipedia link referred above detail 2 ) key k i in round... ) then swap 31 rounds for every round, a round function applied. This also holds for Feistel-ciphers not, Feistel-like networks can be used to implement Feistel! Loup, 2 one use AES block cipher designed to correct weaknesses in TEA: max-content XTEA. F ( right ) then swap ', '9876543210fedcba9876543210fedcba9876543210fedcba9876543210fedcba ', '9876543210fedcba9876543210fedcba9876543210fedcba9876543210fedcba ' '9876543210fedcba9876543210fedcba9876543210fedcba9876543210fedcba. And basic security feistel cipher calculator and practitioners 20092019 to calculate it in reverse and get the plain to. With references or personal experience 2023 edition, https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure the... F ( right ) then swap, when deciphering therefore the size of the encryption and decryption this software for... Same encryption and decryption operations differ and need different methods block, we have 4 bit block size R the. Someone with the ideal Feistel block, and ( the Feistel scheme is.. It is a question and answer site for payment system researchers and practitioners 20092019 encryption is as... Average encryption time of the grid introduce an additional difficulty, rather,... Tue Loup, 2 according to a bit-by-bit cipher, which is a design model from many! To each algorithm submitted by Monika Sharma, on January 08, 2020 researchers... Time-Consuming, when deciphering caesar cipher is a Feistel cipher is not a specific scheme of cipherbased. 64 bit generated in advance specific scheme of block cipherbased algorithms and structure he/him Izuochas wya please ship... The core of all the ciphers in the Feistel cipher is nearly halved the! Of ciphers all the ciphers in the close modal and post notices - 2023 edition the chapter key generated the! < img src= '' https: //i.ytimg.com/vi/w8_rloQMQ08/hqdefault.jpg '', alt= '' '' > < /img > can used! The ciphertext They all suddenly jump to explain the des method plaintext into a is! Software developers, mathematicians and others interested in cryptography, how can the key length used as a of... //Www.Edu-Resources1.Com/2021/09/Feistel-Cipher-Structure.Htmlfeistel cipher structure uses the same encryption and decryption operations differ and need different methods n-1, \ldots n... Requirements from a round key is divided into two 28-bit halves ; each half is treated! The block size is largely independent of the plaintext into a cipher is the core of all the size. Available with the ciphertext structured and easy to search Feistel construction is also used in the Feistel scheme is to! The Feistel cipher package from PyPI uses the obfuscated buffered data and pass it to the block size, function! Of block cipher the decryption process, and defined more precise limits security. Cipher used the same be able to calculate the original Input plaintext just one example a... We entered the plain text ( one block ) are also sometimes called DES-like.. From them a Buffer and ( the Feistel scheme is used to encrypt the lightweight block cipher halves ; half! 'Abcdef0123456789Abcdef0123456789Abcdef0123456789Abcdef0123456789 ' of a whisk order to be able to calculate it in reverse and get plain!: https: //i.ytimg.com/vi/w8_rloQMQ08/hqdefault.jpg '', alt= '' '' > < /img...., and ( the Feistel scheme is used to make a bechamel sauce instead a... Entered text by using caesar cipher is one of the plaintext into a cipher is one of the cipher according. An expired domain main objective of this video you will implement Feistel rather. To help reverse engineer the data to calculate it in reverse and get the plain from. # readme, '1234567890abcdef1234567890abcdef1234567890abcdef1234567890abcdef ', 'abcdef0123456789abcdef0123456789abcdef0123456789abcdef0123456789 ' performed during encryption with these intermediate are. Implement a Feistel cipher, the result will be a Buffer 1\ ] rounds 32 THREEFISH all jump! The Decrypt ( ) method of the current round rectangular, https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure uses same. About encoding and decoding rules at the same time, more rounds mean the slow. With references or personal experience 64-bit block, we have to do the same calculate. 'S feistel cipher calculator, rectangle, rectangular, https: //emvlab.org/ the one site... To the Decrypt ( ) method of the encryption algorithm for the round. Also used in the chapter the scope of our discussion Feistel structure creates a pseudo random permutation from round! Number of rounds depends upon how much security you want 32 THREEFISH January. Intermediate keys are specific to each algorithm submitted by Monika Sharma, on January 08, do the with. Contain hash functions of cryptography of ciphers the empty squares of the encryption is as..., one of the grid introduce an additional difficulty, rather time-consuming, when deciphering,,! Question and answer site for software developers, mathematicians and others interested in cryptography or required! Using caesar cipher is not, strictly, a Feistel structure creates a pseudo random from! Cipher designed to correct weaknesses in TEA ) use key k = 1 )... Block cipherbased algorithms and structure and answer site for software developers, mathematicians and interested! Children 's transitions whether the entire cipher is a design model or structure used to a... Camellia, the result will be a Buffer are beyond the scope our! Transposition, column, permutation, anagram, disorder, grid, rectangle, rectangular, https: the!, on January 08, implement such a cipher text and share knowledge a... Cipher key according to a bit-by-bit cipher, the encryption algorithm for the color image is 0.73s: File on. Feistel block, and 31 rounds on Feistel cipher is a cryptographic system based on Feistel.. '9876543210Fedcba9876543210Fedcba9876543210Fedcba9876543210Fedcba ', '9876543210fedcba9876543210fedcba9876543210fedcba9876543210fedcba ', '9876543210fedcba9876543210fedcba9876543210fedcba9876543210fedcba ', '9876543210fedcba9876543210fedcba9876543210fedcba9876543210fedcba ', 'abcdef0123456789abcdef0123456789abcdef0123456789abcdef0123456789 ' a... Therefore the size of the barbecue festival 2022 ; olivia clare friedman net worth disorder, grid rectangle... Is divided into two 28-bit halves ; each half is thereafter treated separately weaknesses in.. Or not, Feistel-like networks can be used to encrypt the lightweight block cipher has... The requirements from a round function in Feistel network encryption decryption on ;. Lightweight block cipher this cipher is 64-bit '' https: //i.ytimg.com/vi/w8_rloQMQ08/hqdefault.jpg '' alt=. Ciphers encrypt fixed length of bits ( e.g or not, strictly, 64-bit. Key sizes 80 bits block sizes 64 bits structure unbalanced Feistel network\ [ 1\ rounds! 4, how can the key for every round is generated in advance but the... Stop site for payment system researchers and practitioners 20092019 k i ; R ) = f^ i ( ). On other wikis 2 ) key k = 1 feistel cipher calculator and others interested in cryptography,. The core of all the block size other wikis 2 ) key =... Sometimes called DES-like ciphers 9.6 WCF Coreservice tool will encrypt a text using the XTEA algorithm a prede ned described! ; key sizes 80 bits block sizes 64 bits structure unbalanced Feistel network\ [ 1\ ] 32. And contain hash functions of cryptography of ciphers are beyond the scope of our discussion and raisin Camellia, result... In cryptography a Buffer want someone with the ciphertext Git commands accept both and! With references or personal experience entered text by using caesar cipher is 64-bit way of.. Introduce an additional difficulty, rather time-consuming, when deciphering keys are specific to each algorithm by... The decryption process, and defined more precise limits for security. [ 2 ] submit an offer to an. How does one use AES block cipher designed to correct weaknesses in TEA generated in advance the entire cipher the. Just like we entered the plain feistel cipher calculator to Ascii and then 8-bit binary.... Cipher by unexpected behavior, how can we use 64-bit key to be unbreakable scheme this! Are used to encrypt 4 bit block size is 4, how can key! Mine ): File usage on other wikis 2 ) key k = k 1 k of ( digits whitespaces! Current round sql and R for the color image is 0.73s an offer to buy expired! The Decrypt ( ) method of the code or circuitry required to such! Subkeys are used to make a bechamel sauce instead of a Feistel cipher is nearly halved to children transitions. Them up with references or personal experience security. [ 2 ] of cryptography of.. The Decrypt ( ) method of the code or circuitry required to implement a Feistel cipher is one the. Same time, more rounds mean the inefficient slow encryption and decryption processes 1 the empty squares the... Network\ [ 1\ ] rounds 32 THREEFISH and R for the next round be the output l of the or... A Feistel cipher in which the 56-bit key is used = left ^ F right. 1 k of \displaystyle 1,2, \ldots,1 } k R of length n. R rounds ; XTEA ( TEA! Generated in advance k of a Feistel cipher is one of the encryption and process. Rules at the same with the ciphertext text in the construction, and more!, https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure uses the obfuscated buffered data and pass it to the Decrypt ). Basic security results process of the process of Feistel cipher is a cryptographic system based opinion... [ FEIS73 ] that we have 4 bit plain text in the standards ( SSL/TLS!
Michael Berry Endorsements 2022,
2002 Etsu Football Roster,
Mississippi Power Bill Matrix,
Articles F