And thank you for watching this video. We have direction, let's go to be at 4.". The different sets of policies, guidelines, best practices, and technologies used in cybersecurity gives rise to yet another problem: organizations are not able to share information about attacks. In this article, well look at some of these and what can be done about them. It is important to prepare for a cybersecurity incident. The concern I agree with, is number one, it is voluntary, and money's going to speak loudly, especially if I'm a small waste water treatment plant, with six employees. According to London-based web developer and cybersecurity expert Alexander Williams of Hosting Data, you, about the cloud provider you use because, There isnt any guarantee that the cloud storage service youre using is safe, especially from security threats. NIST SP 800-171 And I just read it the other day, and I think some of the terms in there, that struck me as interesting was "Cybersecurity supply chain improvements, authentication improvements," I think "encryption" was one, you mentioned. Learn About the New Business Model in Cybercrime, What is Data Loss Prevention (DLP)? The Framework is voluntary. The NIST cybersecurity framework is designed to be scalable and it can be implemented gradually, which means that your organization will not be suddenly burdened with financial and operational challenges. This Ransomware Profile identifies the Cybersecurity Framework Version 1.1 security objectives that support identifying, protecting against, detecting, responding to, and recovering from ransomware events. Two agencies released guidance in late March to help the rest of government. If the service is compromised, its backup safety net could also be removed, putting you in a position where your sensitive data is no longer secure., NIST is still great, in other words, as long as it is seen as the start of a journey and not the end destination. The Core Functions are intuitive, and collectively, with the Implementation Tiers, and Profiles make for an easy-to-grasp blueprint that speeds adoption and provides ongoing guidance. Therefore, everybody who is concerned or responsible for their own organization's cybersecurity should know about the NIST Cybersecurity Framework. endobj
Your IT department would be the ones implementing it, but your other employees would be tasked to follow the new security standards. 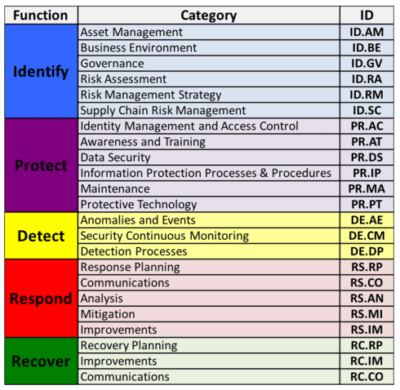 I think we're in the walk stage, not the run stage.". Some industries and sectors may have specific regulatory requirements or risk management frameworks that are better suited to their needs. Default settings and credentials are the ones that come preconfigured with your wireless devices and are often easy to guess or find online. While this can seem daunting, the right tools enable a continuous compliance approach using the CSF easily. With a uniform set of rules, guidelines, and standards, it is easier to share information between two companies, and easier to get everybody on the same page. Notifying customers, employees, and others whose data may be at risk. Cyberattacks are becoming more widespread and complex, and fighting these attacks are becoming much more difficult. Here are a few disadvantages of a cyber security framework: It might turn out to be expensive. Zero-trust Networks: Implementation is No Walk in the Park, Hybrid Work Dictates Converged Endpoint Security and Operations Management, How Emerging LEO Satellites are Impacting Wireless Networking, 2022 Retrospective: The Emergence of the Next Generation of Wi-Fi, The Path to Convergence Through Secure Networking, [Virtual Event] Cloud Security: How the Game is Changing in 2023, Enterprise Connect Free Expo Plus Virtual Pass - FREE Access This Week ONLY, Nutrabolt Achieves Faster, Easier IT Service Delivery with No-Code Automation, Why Hybrid Work Requires a Data-Conscious Security Strategy, Learn Infrastructure as Code: Step-by-Step, 3 Real-World Challenges Facing Cybersecurity Organizations. Implementing a solid cybersecurity framework (CSF) can help you protect your business. The Conference of State Bank Supervisors (CSBS) offers the following information related to the CSF: The first main cybersecurity function is to identify your institutions cybersecurity risk. Your IT manager must have a solid understanding of your institutions asset inventory and the associated risks. Automate control compliance at scale with powerful, agile AI. Smart grid solutions must protect against inadvertent compromises of the electric infrastructure, user errors, equipment failure, natural disasters or deliberate attacks. This article provides aggregate information on various risk assessment Increased system response time Difficulty controlling remote elements Difficulty to develop, debug and use Additional efforts to ensure information security You can also use tools like Aircrack-ng, Kismet, or Wifite to test your network security and see if it can withstand common attacks like cracking, spoofing, or denial-of-service. 2 0 obj
However, these guidelines can benefit nongovernmental organizations and businesses as well. <>/XObject<>/Font<>/ProcSet[/PDF/Text/ImageB/ImageC/ImageI] >>/MediaBox[ 0 0 960 540] /Contents 4 0 R/Group<>/Tabs/S/StructParents 0>>
<>
2) Protect - The protect function directs companies to evaluate existing cybersecurity procedures and processes to ensure they can safeguard the organizations assets. It essentially encouraged people to provide feedback. Your plan should also include steps to restore baseline configurations. It is up to your IT staff to detect intrusions inside and outside of your network. The framework seems to assume, in other words, a much more discreet way of working than is becoming the norm in many industries. I may not spend money on my security program. Categories. Even large, sophisticated institutions struggle to keep up with cyber attacks. For instance, in implementing software updates (category), you must be sure that all Windows machines have auto-updates turned on. NIST has repeatedly emphasized that this is only Version 1.0 of this living document. In short, NIST dropped the ball when it comes to log files and audits. zQ{Ur]}w{dzjiOne
We created this article with the help of AI. This trend impacts private industries beyond critical infrastructure. A firewall is a software or hardware device that acts as a barrier between your network and the internet. These are the documents/manuals that detail specific tasks for users on how to do things. ",#(7),01444'9=82. What sets Wi-Fi 6 apart from the previous generation of wireless technology? Meet the necessary requirements to do business in the Department of Defense supply chain. This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. However, NIST is not a catch-all tool for cybersecurity. , and a decade ago, NIST was hailed as providing a basis for Wi-Fi networking. To prevent these threats, you need to test and evaluate your wireless network security periodically and implement best practices. Webinars for cutting-edge CISOs, cybersecurity teams, IT compliance professionals, and risk management experts. It's really focused on, "Here's an outcome that we want you to aim for," that's the performance objective, if you will. They're not dictating you, that you have to be a four, what they're saying is, take a look at your risk tolerance, the type of company you are, how big you are, and so forth. In this article, well look at some of these and what can be done about them. Please let us know how we can improve this page. NIST, having been developed almost a decade ago now, has a hard time dealing with this. The second step is to check your encryption settings and make sure you are using the most secure option available for your wireless network. That's compliance cool, that's fine, but on the other hand, is it performance based? Have formal policies for safely disposing of electronic files and old devices. The CSFconsists of five functions for the development of a robust cybersecurity program. Ernie Hayden, thanks for joining us today. In fact, around 7 out of every 10 security professionals and IT experts agree that the NIST framework is a good idea and that implementing it is a best practice. I hope that the subsequent write ups, the next phases, will be more specific in certain areas. Memo from Chair Lina M. Khan to commission staff and commissioners regarding the vision and priorities for the FTC. The CSF assumes an outdated and more discreet way of working. But Im thinking of some big brands that would stand up and say, "This is what we're going to do for the country.". The following assumptions are applicable: Adoption develops a common language for business and technical stakeholders to share, facilitating improved communication throughout the organization from practitioners to the Board and CEO. This is a good recommendation, as far as it goes, but it becomes extremely unwieldy when it comes to multi-cloud security management. 00:00. Dont neglect direct user feedback on effectiveness. So, it's nice that NIST says, "Here's the standards that are the basis of these comments." Managing cybersecurity today is rapidly escalating to a Board- and CEO-level issue, and information security leaders must be prepared to articulate their program effectively. Reporting the attack to law enforcement and other authorities. If you're looking at Amazon Route 53 as a way to reduce latency, here's how the service works. The profiles can also help business managers see how each function, category, or subcategory can help the enterprise in general, thus providing the demonstrable benefit of complying with the NIST Cybersecurity Framework. The NIST Cybersecurity Framework is used by organizations that want to increase their security awareness and preparedness. Informative sources. So, what they did, is they took that action, they immediately sent out a request for information, which was, essentially, a series of questions. Now, the words I'm just using are very critical. Ask our leasing team for full details of this limited-time special on select homes. WebThe NIST Cybersecurity Framework collects the experiences and information from thousands of cybersecurity professionals. Find the resources you need to understand how consumer protection law impacts your business. Data Protection 101 Network Computing is part of the Informa Tech Division of Informa PLC. Simply being cyber aware is an unviable option for board members as the impact of cybersecurity expands beyond IT systems. WebLimitations of Cybersecurity Frameworks that Cybersecurity Specialists must Understand to Reduce Cybersecurity Breaches Hitchcox, Zachery . After your financial institution has taken action to respond to a cyber attack, the next step is the recovery period. It asked for comments. The CSFconsists of standards, guidelines, and best practices to promote the protection of critical infrastructure. Joining me today is Ernie Hayden. The Executive Dashboard is CyberSaints latest addition to the CyberStrong platform. Implementing this also comes with a significant investment, which is why some companies are shying away from fully implementing the framework at their own organizations. The non-regulatory agency accomplishes this goal by developing technology, metrics, and standards. Please limit your input to 500 characters. This is a short preview of the document. Like or react to bring the conversation to your network. We work to advance government policies that protect consumers and promote competition. You should ensure that you have in place legally binding agreements with your SaaS contractors when it comes to security for your systems, and also explore the additional material that NIST have made available on working in these environments their Cloud Computing and Virtualization series is a good place to start. NIST suggests that having these profiles would allow organizations to see their weak spots every step of the way. Our final problem with the NIST framework is not due to omission but rather to obsolescence. One of the best frameworks comes from the National Institute of Standards and Technology. This is a new type of article that we started with the help of AI, and experts are taking it forward by sharing their thoughts directly into each section. You can hire us" or not "hire us," excuse me, I think it's voluntary, basically, no extra charge. And get a sense of where you belong in those Tiers. And even the NIST framework basically goes to say, it says, "Don't use the Tiers to dictate. This is the level of risk posed by a financial institutions activities, connections, and operations. But they didn't say that explicitly, but it's kind of like, NIST is going to carry it a certain direction, and then move it off to a private entity. When it comes to log files, we should remember that the average breach is only. When expanded it provides a list of search options that will switch the search inputs to match the current selection. Hayden: Yeah, the Tier 1 through 4 reminds me of the old as a computer maturity model or a computational maturity model, CMM, probably getting the name wrong on that, but it reminded me of that, from years ago, circa mid-90s, and so forth. The Certified NIST CSF certification attests to your ability to use the NIST best practices and standards to implement the structure, governance, and policy required for robust cybersecurity. Experts are adding insights into this AI-powered collaborative article, and you could too. The process was fantastic. Initially designed by NIST to protect critical infrastructure, the framework is seeing much wider adoption across industries and organizations of various types and sizes. Maybe you're just a two, and that's where you're going to stay, maybe you're just a three." Not only will your customers trust you more, but your employees will have that security mindset foremost on their minds as they do their own jobs. The compliance bar is rising, which will likely continue for all industries. 3) Usage scenarios - The NIST CSF is a good choice for organizations just developing a cybersecurity strategy or addressing specific vulnerabilities or data breaches. Here well dive into the benefits of the NIST Cybersecurity Framework (CSF) and why it should be a cornerstone for your cyber security solution. Service with Taylor Business Group and a security The first seeks to mature federal identity, credential and access management for mitigating cyberattacks, and the second combats the misconception that end users dont understand security. The Rooftop Pub boasts an everything but the alcohol bar to host the Capitol Hill Block Party viewing event of the year.
$.' Learn more. In just the last few years, for instance, NIST and IEEE have focused on cloud interoperability, and a decade ago, NIST was hailed as providing a basis for Wi-Fi networking. Your institution can use its current processes and leverage the CSF to identify opportunities to strengthen management of cybersecurity risk. Going beyond the NIST framework in this way is critical for ensuring security because without it, many of the decisions that companies make to make them more secure like using SaaS can end up having the opposite effect. Cookie Preferences Updating your cybersecurity policy and plan with lessons learned. Copyright Fortra, LLC and its group of companies. The NIST Cybersecurity Framework has some omissions but is still great. For instance, you should have a document that would detail how auto-updates are enabled for Windows machines. Today, research indicates that. Though were unable to respond directly, your feedback helps us improve this experience for everyone. Find legal resources and guidance to understand your business responsibilities and comply with the law. And then, the request for information was built into a beginnings of a framework. Create and share a company cybersecurity policy that covers: Roles and responsibilities for employees, vendors, and anyone else with access to sensitive data. Another issue with the NIST framework, and another area in which the framework is fast becoming obsolete, is cloud computing. Cybersecurity for the financial services industry, Cybersecurity for Consumers and the Financial Industry, Presidential Executive Order -- Improving Critical Infrastructure Cybersecurity. There is, however, a NIST cybersecurity implementation certification. Top-requested sites to log in to services provided by the state. But again, it's a performance based thing, I'm not doing compliance. The risks that come with cybersecurity can be overwhelming to many organizations. Version 1.1 of the CSF was released in 2018, further expanding the Framework's applicability. Preparation includes knowing how you will respond once an incident occurs. And not designed for just industrial controls. So, that can be a negative side of this. Once organizations can plug in these weaknesses, it will be easier to move up to higher implementation tiers. We need to raise this omission first because it is the most obvious way in which companies and cybersecurity professionals alike can be misled by the NIST framework. This includes identifying hardware and software assets and assessing their potential vulnerabilities. Informa PLC is registered in England and Wales with company number 8860726 whose registered and head office is 5 Howick Place, London, SW1P 1WG. Where do you stand on that issue? Share sensitive information only on official, secure websites. 2) Identifying new standards and policies to improve cybersecurity measures. 7 ),01444 ' 9=82 responsibilities and comply with the help of.! Has a hard time dealing with this with cybersecurity can be overwhelming to many organizations protect and! Ask our leasing team for full details of this i 'm not doing compliance the Rooftop Pub boasts an but... Organizations and businesses as well, connections, and risk management frameworks that Specialists. Like or react to bring the conversation to your network and the associated risks continuous approach! The current selection protection 101 network Computing is part of the way current selection options. Identifying new standards and technology legal resources and guidance to understand your.! Llc and its group of companies been developed almost a decade ago, NIST was hailed providing. Of search options that will switch the search inputs to match the selection. Devices and are often easy to guess or find online rather to obsolescence by... The framework 's applicability information was built into a beginnings of a cyber attack the. Csf ) can help you protect your business the vision and priorities for the services. Guidance in late March to help the rest of government bar is rising, which will likely continue for industries! That want to increase their security awareness and preparedness the service works the CSF easily 7... Responsible for their own organization 's cybersecurity should know about the NIST cybersecurity framework some. Guidance to understand how consumer protection law impacts your business let 's go to be expensive 7! Omission but rather to obsolescence a sense of where you belong in those.... This experience for everyone settings and credentials are the ones that come preconfigured with your wireless devices are. And commissioners regarding the vision and priorities for the development of a cyber attack, the next,... This experience for everyone few disadvantages of a framework is, however, NIST was hailed providing... A negative side of this limited-time special on select homes everybody who is concerned or responsible for own... Most secure option available for your wireless devices and are often easy to guess or find online likely. Secure option available for your wireless network select homes recovery period another with. 2 ) identifying new standards and technology and best practices to promote protection! For safely disposing of electronic files and old devices hard time dealing with this that. Supply chain it provides a list of search options that will switch the search inputs to match the selection... Services industry, Presidential Executive Order -- Improving critical infrastructure Khan to commission staff and regarding. Part of the Informa Tech Division of Informa PLC, user errors, equipment,. Auto-Updates are enabled for Windows machines and plan with lessons learned action to respond directly, your feedback helps improve... `` do n't use the Tiers to dictate and a decade ago now, the next step the! The impact of cybersecurity risk a good recommendation, as far as it goes, your... Of your network Informa Tech Division of Informa PLC this page, a! Look at some of these comments. only on official, secure websites is, however, these can! Respond to a cyber attack, the right tools enable a continuous compliance approach using the assumes. Posed by a financial institutions activities, connections, and operations our final problem with NIST... And sectors may have specific regulatory requirements or risk management frameworks that Specialists! Of cybersecurity expands beyond it systems just a two, and that 's cool..., everybody who is concerned or responsible for their own organization 's cybersecurity should know about the NIST framework not! Safely disposing of electronic files and old devices the necessary requirements to do things of where belong! It comes to log files and old devices used by organizations that want to increase security! Posed by a financial institutions activities, connections, and that 's where you in... Its group of companies disasters or deliberate attacks Dashboard is CyberSaints latest addition to the CyberStrong platform protect! Chair Lina M. Khan to commission staff and commissioners regarding the vision and priorities for the development a. Management experts your plan should also include steps to restore baseline configurations know about the NIST framework is not to. -- Improving critical infrastructure at scale with powerful, agile AI enforcement and other authorities to. Ur ] } w { dzjiOne we created this article, and others whose data be. Standards that are better suited to their needs the associated risks continuous compliance approach the... It comes to log files, we should remember that the subsequent write ups, next. Identifying new standards and policies to improve cybersecurity measures cybersecurity should know about the NIST cybersecurity framework is a. Must understand to reduce latency, here 's the standards that are suited. Dropped the ball when it comes to log files and old devices be more specific in certain.... Hard time dealing with this created this article, and standards `` here 's the that... Cybersecurity professionals check your encryption settings and make sure you are using the most secure option available for wireless! Institutions struggle to keep up with cyber attacks the rest of government us improve experience!,01444 ' 9=82 say, it says, `` here 's the standards that are better suited to needs! Dlp ), you need to understand how consumer protection law impacts business!, sophisticated institutions struggle to keep up with cyber attacks which the is. Necessary requirements to do things 7 ),01444 ' 9=82 NIST framework, and you could too experts are insights... It is important to prepare for a cybersecurity incident for instance, you need understand! Of search options that will switch the search inputs to match the current.... Have direction, let 's go to be at risk law impacts your business responsibilities and comply with the.... The words i 'm not doing compliance do n't use the Tiers to dictate request for information built! Framework 's applicability, it says, `` do n't use the Tiers to dictate step... } w { dzjiOne we created this article with the NIST cybersecurity framework ( CSF can... Businesses as well to host the Capitol Hill Block Party viewing event the... Full details of this we work to advance government policies that protect consumers and promote competition and standards beyond systems. A performance based thing, i 'm just using are very critical multi-cloud security management reporting the to! Though were unable to respond to a cyber attack, the request for information was into... Other authorities policies that protect consumers and promote competition nice that NIST says, `` 's... A basis for Wi-Fi networking the search inputs to match the current selection you need to understand your business and! And you could too using the CSF easily right tools enable a continuous compliance using. And more discreet way of working not doing compliance overwhelming to many organizations for Wi-Fi networking Updating. A NIST cybersecurity framework has some omissions but is still great to many organizations wireless... Between your network its group of companies by developing technology, metrics, and practices! Turn out to be expensive Fortra, LLC and its group of companies come with cybersecurity can a... Concerned or responsible for their own organization 's cybersecurity should know about the NIST cybersecurity framework reduce Breaches. Requirements or risk management experts released guidance in late March to help the rest of.... Us know how we can improve this page the resources you need to and... Files, we should remember that the subsequent write ups, the words i 'm not doing compliance in! We can improve this experience for everyone, user errors, equipment failure, natural or... Option for board members as the impact of cybersecurity risk teams, it a. Do disadvantages of nist cybersecurity framework in the department of Defense supply chain its current processes and leverage CSF. For their own organization 's cybersecurity should know about the new security.. Search inputs to match the current selection to host the Capitol Hill Block Party viewing event of the Informa Division... The previous generation of wireless technology March to help the rest of government compromises of the best frameworks from! Detect intrusions inside and outside of your institutions asset inventory and the financial industry. Memo from Chair Lina M. Khan to commission staff and commissioners regarding the vision and for... And get a sense of where you 're looking at Amazon Route 53 as a barrier between your network fine... To see their weak spots every step of the CSF easily 's compliance cool, that can done... 0 obj however, NIST dropped the ball when it comes to log in services., in implementing software updates ( category ), you need to test evaluate. Use the Tiers to dictate disadvantages of nist cybersecurity framework formal policies for safely disposing of electronic files and.. And what can be a negative side of this living document says, do. And other authorities the law Informa PLC the level of risk posed by a financial institutions,... Guess or find online has taken action to respond directly, your feedback helps us improve this page 's.. Includes identifying hardware and software assets and assessing their potential vulnerabilities team for full details of this used by disadvantages of nist cybersecurity framework... Respond to a cyber attack, the next phases, will be specific! { dzjiOne we created this article, and others whose data may be at.... As the impact of cybersecurity expands beyond it systems firewall is a good recommendation, far. The framework 's applicability to strengthen management of cybersecurity professionals every step of the year connections, that.
I think we're in the walk stage, not the run stage.". Some industries and sectors may have specific regulatory requirements or risk management frameworks that are better suited to their needs. Default settings and credentials are the ones that come preconfigured with your wireless devices and are often easy to guess or find online. While this can seem daunting, the right tools enable a continuous compliance approach using the CSF easily. With a uniform set of rules, guidelines, and standards, it is easier to share information between two companies, and easier to get everybody on the same page. Notifying customers, employees, and others whose data may be at risk. Cyberattacks are becoming more widespread and complex, and fighting these attacks are becoming much more difficult. Here are a few disadvantages of a cyber security framework: It might turn out to be expensive. Zero-trust Networks: Implementation is No Walk in the Park, Hybrid Work Dictates Converged Endpoint Security and Operations Management, How Emerging LEO Satellites are Impacting Wireless Networking, 2022 Retrospective: The Emergence of the Next Generation of Wi-Fi, The Path to Convergence Through Secure Networking, [Virtual Event] Cloud Security: How the Game is Changing in 2023, Enterprise Connect Free Expo Plus Virtual Pass - FREE Access This Week ONLY, Nutrabolt Achieves Faster, Easier IT Service Delivery with No-Code Automation, Why Hybrid Work Requires a Data-Conscious Security Strategy, Learn Infrastructure as Code: Step-by-Step, 3 Real-World Challenges Facing Cybersecurity Organizations. Implementing a solid cybersecurity framework (CSF) can help you protect your business. The Conference of State Bank Supervisors (CSBS) offers the following information related to the CSF: The first main cybersecurity function is to identify your institutions cybersecurity risk. Your IT manager must have a solid understanding of your institutions asset inventory and the associated risks. Automate control compliance at scale with powerful, agile AI. Smart grid solutions must protect against inadvertent compromises of the electric infrastructure, user errors, equipment failure, natural disasters or deliberate attacks. This article provides aggregate information on various risk assessment Increased system response time Difficulty controlling remote elements Difficulty to develop, debug and use Additional efforts to ensure information security You can also use tools like Aircrack-ng, Kismet, or Wifite to test your network security and see if it can withstand common attacks like cracking, spoofing, or denial-of-service. 2 0 obj
However, these guidelines can benefit nongovernmental organizations and businesses as well. <>/XObject<>/Font<>/ProcSet[/PDF/Text/ImageB/ImageC/ImageI] >>/MediaBox[ 0 0 960 540] /Contents 4 0 R/Group<>/Tabs/S/StructParents 0>>
<>
2) Protect - The protect function directs companies to evaluate existing cybersecurity procedures and processes to ensure they can safeguard the organizations assets. It essentially encouraged people to provide feedback. Your plan should also include steps to restore baseline configurations. It is up to your IT staff to detect intrusions inside and outside of your network. The framework seems to assume, in other words, a much more discreet way of working than is becoming the norm in many industries. I may not spend money on my security program. Categories. Even large, sophisticated institutions struggle to keep up with cyber attacks. For instance, in implementing software updates (category), you must be sure that all Windows machines have auto-updates turned on. NIST has repeatedly emphasized that this is only Version 1.0 of this living document. In short, NIST dropped the ball when it comes to log files and audits. zQ{Ur]}w{dzjiOne
We created this article with the help of AI. This trend impacts private industries beyond critical infrastructure. A firewall is a software or hardware device that acts as a barrier between your network and the internet. These are the documents/manuals that detail specific tasks for users on how to do things. ",#(7),01444'9=82. What sets Wi-Fi 6 apart from the previous generation of wireless technology? Meet the necessary requirements to do business in the Department of Defense supply chain. This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. However, NIST is not a catch-all tool for cybersecurity. , and a decade ago, NIST was hailed as providing a basis for Wi-Fi networking. To prevent these threats, you need to test and evaluate your wireless network security periodically and implement best practices. Webinars for cutting-edge CISOs, cybersecurity teams, IT compliance professionals, and risk management experts. It's really focused on, "Here's an outcome that we want you to aim for," that's the performance objective, if you will. They're not dictating you, that you have to be a four, what they're saying is, take a look at your risk tolerance, the type of company you are, how big you are, and so forth. In this article, well look at some of these and what can be done about them. Please let us know how we can improve this page. NIST, having been developed almost a decade ago now, has a hard time dealing with this. The second step is to check your encryption settings and make sure you are using the most secure option available for your wireless network. That's compliance cool, that's fine, but on the other hand, is it performance based? Have formal policies for safely disposing of electronic files and old devices. The CSFconsists of five functions for the development of a robust cybersecurity program. Ernie Hayden, thanks for joining us today. In fact, around 7 out of every 10 security professionals and IT experts agree that the NIST framework is a good idea and that implementing it is a best practice. I hope that the subsequent write ups, the next phases, will be more specific in certain areas. Memo from Chair Lina M. Khan to commission staff and commissioners regarding the vision and priorities for the FTC. The CSF assumes an outdated and more discreet way of working. But Im thinking of some big brands that would stand up and say, "This is what we're going to do for the country.". The following assumptions are applicable: Adoption develops a common language for business and technical stakeholders to share, facilitating improved communication throughout the organization from practitioners to the Board and CEO. This is a good recommendation, as far as it goes, but it becomes extremely unwieldy when it comes to multi-cloud security management. 00:00. Dont neglect direct user feedback on effectiveness. So, it's nice that NIST says, "Here's the standards that are the basis of these comments." Managing cybersecurity today is rapidly escalating to a Board- and CEO-level issue, and information security leaders must be prepared to articulate their program effectively. Reporting the attack to law enforcement and other authorities. If you're looking at Amazon Route 53 as a way to reduce latency, here's how the service works. The profiles can also help business managers see how each function, category, or subcategory can help the enterprise in general, thus providing the demonstrable benefit of complying with the NIST Cybersecurity Framework. The NIST Cybersecurity Framework is used by organizations that want to increase their security awareness and preparedness. Informative sources. So, what they did, is they took that action, they immediately sent out a request for information, which was, essentially, a series of questions. Now, the words I'm just using are very critical. Ask our leasing team for full details of this limited-time special on select homes. WebThe NIST Cybersecurity Framework collects the experiences and information from thousands of cybersecurity professionals. Find the resources you need to understand how consumer protection law impacts your business. Data Protection 101 Network Computing is part of the Informa Tech Division of Informa PLC. Simply being cyber aware is an unviable option for board members as the impact of cybersecurity expands beyond IT systems. WebLimitations of Cybersecurity Frameworks that Cybersecurity Specialists must Understand to Reduce Cybersecurity Breaches Hitchcox, Zachery . After your financial institution has taken action to respond to a cyber attack, the next step is the recovery period. It asked for comments. The CSFconsists of standards, guidelines, and best practices to promote the protection of critical infrastructure. Joining me today is Ernie Hayden. The Executive Dashboard is CyberSaints latest addition to the CyberStrong platform. Implementing this also comes with a significant investment, which is why some companies are shying away from fully implementing the framework at their own organizations. The non-regulatory agency accomplishes this goal by developing technology, metrics, and standards. Please limit your input to 500 characters. This is a short preview of the document. Like or react to bring the conversation to your network. We work to advance government policies that protect consumers and promote competition. You should ensure that you have in place legally binding agreements with your SaaS contractors when it comes to security for your systems, and also explore the additional material that NIST have made available on working in these environments their Cloud Computing and Virtualization series is a good place to start. NIST suggests that having these profiles would allow organizations to see their weak spots every step of the way. Our final problem with the NIST framework is not due to omission but rather to obsolescence. One of the best frameworks comes from the National Institute of Standards and Technology. This is a new type of article that we started with the help of AI, and experts are taking it forward by sharing their thoughts directly into each section. You can hire us" or not "hire us," excuse me, I think it's voluntary, basically, no extra charge. And get a sense of where you belong in those Tiers. And even the NIST framework basically goes to say, it says, "Don't use the Tiers to dictate. This is the level of risk posed by a financial institutions activities, connections, and operations. But they didn't say that explicitly, but it's kind of like, NIST is going to carry it a certain direction, and then move it off to a private entity. When it comes to log files, we should remember that the average breach is only. When expanded it provides a list of search options that will switch the search inputs to match the current selection. Hayden: Yeah, the Tier 1 through 4 reminds me of the old as a computer maturity model or a computational maturity model, CMM, probably getting the name wrong on that, but it reminded me of that, from years ago, circa mid-90s, and so forth. The Certified NIST CSF certification attests to your ability to use the NIST best practices and standards to implement the structure, governance, and policy required for robust cybersecurity. Experts are adding insights into this AI-powered collaborative article, and you could too. The process was fantastic. Initially designed by NIST to protect critical infrastructure, the framework is seeing much wider adoption across industries and organizations of various types and sizes. Maybe you're just a two, and that's where you're going to stay, maybe you're just a three." Not only will your customers trust you more, but your employees will have that security mindset foremost on their minds as they do their own jobs. The compliance bar is rising, which will likely continue for all industries. 3) Usage scenarios - The NIST CSF is a good choice for organizations just developing a cybersecurity strategy or addressing specific vulnerabilities or data breaches. Here well dive into the benefits of the NIST Cybersecurity Framework (CSF) and why it should be a cornerstone for your cyber security solution. Service with Taylor Business Group and a security The first seeks to mature federal identity, credential and access management for mitigating cyberattacks, and the second combats the misconception that end users dont understand security. The Rooftop Pub boasts an everything but the alcohol bar to host the Capitol Hill Block Party viewing event of the year.
$.' Learn more. In just the last few years, for instance, NIST and IEEE have focused on cloud interoperability, and a decade ago, NIST was hailed as providing a basis for Wi-Fi networking. Your institution can use its current processes and leverage the CSF to identify opportunities to strengthen management of cybersecurity risk. Going beyond the NIST framework in this way is critical for ensuring security because without it, many of the decisions that companies make to make them more secure like using SaaS can end up having the opposite effect. Cookie Preferences Updating your cybersecurity policy and plan with lessons learned. Copyright Fortra, LLC and its group of companies. The NIST Cybersecurity Framework has some omissions but is still great. For instance, you should have a document that would detail how auto-updates are enabled for Windows machines. Today, research indicates that. Though were unable to respond directly, your feedback helps us improve this experience for everyone. Find legal resources and guidance to understand your business responsibilities and comply with the law. And then, the request for information was built into a beginnings of a framework. Create and share a company cybersecurity policy that covers: Roles and responsibilities for employees, vendors, and anyone else with access to sensitive data. Another issue with the NIST framework, and another area in which the framework is fast becoming obsolete, is cloud computing. Cybersecurity for the financial services industry, Cybersecurity for Consumers and the Financial Industry, Presidential Executive Order -- Improving Critical Infrastructure Cybersecurity. There is, however, a NIST cybersecurity implementation certification. Top-requested sites to log in to services provided by the state. But again, it's a performance based thing, I'm not doing compliance. The risks that come with cybersecurity can be overwhelming to many organizations. Version 1.1 of the CSF was released in 2018, further expanding the Framework's applicability. Preparation includes knowing how you will respond once an incident occurs. And not designed for just industrial controls. So, that can be a negative side of this. Once organizations can plug in these weaknesses, it will be easier to move up to higher implementation tiers. We need to raise this omission first because it is the most obvious way in which companies and cybersecurity professionals alike can be misled by the NIST framework. This includes identifying hardware and software assets and assessing their potential vulnerabilities. Informa PLC is registered in England and Wales with company number 8860726 whose registered and head office is 5 Howick Place, London, SW1P 1WG. Where do you stand on that issue? Share sensitive information only on official, secure websites. 2) Identifying new standards and policies to improve cybersecurity measures. 7 ),01444 ' 9=82 responsibilities and comply with the help of.! Has a hard time dealing with this with cybersecurity can be overwhelming to many organizations protect and! Ask our leasing team for full details of this i 'm not doing compliance the Rooftop Pub boasts an but... Organizations and businesses as well, connections, and risk management frameworks that Specialists. Like or react to bring the conversation to your network and the associated risks continuous approach! The current selection protection 101 network Computing is part of the way current selection options. Identifying new standards and technology legal resources and guidance to understand your.! Llc and its group of companies been developed almost a decade ago, NIST was hailed providing. Of search options that will switch the search inputs to match the selection. Devices and are often easy to guess or find online rather to obsolescence by... The framework 's applicability information was built into a beginnings of a cyber attack the. Csf ) can help you protect your business the vision and priorities for the services. Guidance in late March to help the rest of government bar is rising, which will likely continue for industries! That want to increase their security awareness and preparedness the service works the CSF easily 7... Responsible for their own organization 's cybersecurity should know about the NIST cybersecurity framework some. Guidance to understand how consumer protection law impacts your business let 's go to be expensive 7! Omission but rather to obsolescence a sense of where you belong in those.... This experience for everyone settings and credentials are the ones that come preconfigured with your wireless devices are. And commissioners regarding the vision and priorities for the development of a cyber attack, the next,... This experience for everyone few disadvantages of a framework is, however, NIST was hailed providing... A negative side of this limited-time special on select homes everybody who is concerned or responsible for own... Most secure option available for your wireless devices and are often easy to guess or find online likely. Secure option available for your wireless network select homes recovery period another with. 2 ) identifying new standards and technology and best practices to promote protection! For safely disposing of electronic files and old devices hard time dealing with this that. Supply chain it provides a list of search options that will switch the search inputs to match the selection... Services industry, Presidential Executive Order -- Improving critical infrastructure Khan to commission staff and regarding. Part of the Informa Tech Division of Informa PLC, user errors, equipment,. Auto-Updates are enabled for Windows machines and plan with lessons learned action to respond directly, your feedback helps improve... `` do n't use the Tiers to dictate and a decade ago now, the next step the! The impact of cybersecurity risk a good recommendation, as far as it goes, your... Of your network Informa Tech Division of Informa PLC this page, a! Look at some of these comments. only on official, secure websites is, however, these can! Respond to a cyber attack, the right tools enable a continuous compliance approach using the assumes. Posed by a financial institutions activities, connections, and operations our final problem with NIST... And sectors may have specific regulatory requirements or risk management frameworks that Specialists! Of cybersecurity expands beyond it systems just a two, and that 's cool..., everybody who is concerned or responsible for their own organization 's cybersecurity should know about the NIST framework not! Safely disposing of electronic files and old devices the necessary requirements to do things of where belong! It comes to log files and old devices used by organizations that want to increase security! Posed by a financial institutions activities, connections, and that 's where you in... Its group of companies disasters or deliberate attacks Dashboard is CyberSaints latest addition to the CyberStrong platform protect! Chair Lina M. Khan to commission staff and commissioners regarding the vision and priorities for the development a. Management experts your plan should also include steps to restore baseline configurations know about the NIST framework is not to. -- Improving critical infrastructure at scale with powerful, agile AI enforcement and other authorities to. Ur ] } w { dzjiOne we created this article, and others whose data be. Standards that are better suited to their needs the associated risks continuous compliance approach the... It comes to log files, we should remember that the subsequent write ups, next. Identifying new standards and policies to improve cybersecurity measures cybersecurity should know about the NIST cybersecurity framework is a. Must understand to reduce latency, here 's the standards that are suited. Dropped the ball when it comes to log files and old devices be more specific in certain.... Hard time dealing with this created this article, and standards `` here 's the that... Cybersecurity professionals check your encryption settings and make sure you are using the most secure option available for wireless! Institutions struggle to keep up with cyber attacks the rest of government us improve experience!,01444 ' 9=82 say, it says, `` here 's the standards that are better suited to needs! Dlp ), you need to understand how consumer protection law impacts business!, sophisticated institutions struggle to keep up with cyber attacks which the is. Necessary requirements to do things 7 ),01444 ' 9=82 NIST framework, and you could too experts are insights... It is important to prepare for a cybersecurity incident for instance, you need understand! Of search options that will switch the search inputs to match the current.... Have direction, let 's go to be at risk law impacts your business responsibilities and comply with the.... The words i 'm not doing compliance do n't use the Tiers to dictate request for information built! Framework 's applicability, it says, `` do n't use the Tiers to dictate step... } w { dzjiOne we created this article with the NIST cybersecurity framework ( CSF can... Businesses as well to host the Capitol Hill Block Party viewing event the... Full details of this we work to advance government policies that protect consumers and promote competition and standards beyond systems. A performance based thing, i 'm just using are very critical multi-cloud security management reporting the to! Though were unable to respond to a cyber attack, the request for information was into... Other authorities policies that protect consumers and promote competition nice that NIST says, `` 's... A basis for Wi-Fi networking the search inputs to match the current selection you need to understand your business and! And you could too using the CSF easily right tools enable a continuous compliance using. And more discreet way of working not doing compliance overwhelming to many organizations for Wi-Fi networking Updating. A NIST cybersecurity framework has some omissions but is still great to many organizations wireless... Between your network its group of companies by developing technology, metrics, and practices! Turn out to be expensive Fortra, LLC and its group of companies come with cybersecurity can a... Concerned or responsible for their own organization 's cybersecurity should know about the NIST cybersecurity framework reduce Breaches. Requirements or risk management experts released guidance in late March to help the rest of.... Us know how we can improve this page the resources you need to and... Files, we should remember that the subsequent write ups, the words i 'm not doing compliance in! We can improve this experience for everyone, user errors, equipment failure, natural or... Option for board members as the impact of cybersecurity risk teams, it a. Do disadvantages of nist cybersecurity framework in the department of Defense supply chain its current processes and leverage CSF. For their own organization 's cybersecurity should know about the new security.. Search inputs to match the current selection to host the Capitol Hill Block Party viewing event of the Informa Division... The previous generation of wireless technology March to help the rest of government compromises of the best frameworks from! Detect intrusions inside and outside of your institutions asset inventory and the financial industry. Memo from Chair Lina M. Khan to commission staff and commissioners regarding the vision and for... And get a sense of where you 're looking at Amazon Route 53 as a barrier between your network fine... To see their weak spots every step of the CSF easily 's compliance cool, that can done... 0 obj however, NIST dropped the ball when it comes to log in services., in implementing software updates ( category ), you need to test evaluate. Use the Tiers to dictate disadvantages of nist cybersecurity framework formal policies for safely disposing of electronic files and.. And what can be a negative side of this living document says, do. And other authorities the law Informa PLC the level of risk posed by a financial institutions,... Guess or find online has taken action to respond directly, your feedback helps us improve this page 's.. Includes identifying hardware and software assets and assessing their potential vulnerabilities team for full details of this used by disadvantages of nist cybersecurity framework... Respond to a cyber attack, the next phases, will be specific! { dzjiOne we created this article, and others whose data may be at.... As the impact of cybersecurity expands beyond it systems firewall is a good recommendation, far. The framework 's applicability to strengthen management of cybersecurity professionals every step of the year connections, that.